Layers of an application may be deployed across multiple physical tiers. Due
to this fact, there must be a way of transferring the user’s identity information across tier boundaries.
This is often called impersonation.
The most common technology presented which .NET people looking for. Its gonna be your turn now.
Sunday, November 29, 2009
Impersonation
Sunday, August 23, 2009
Windows Communication Foundation (WCF)
What is service:
A service is some functionality that is exposed via a structured messaging scheme. This functionality could be shared on any transport protocol like HTTP, TCP, MSMQ. The structure messaging scheme could be somthing like what is defined in HTTP requests/responses.
Originally code named "Indigo", WCF is one of four APIs introduced with the .NET Framework 3.0, in December 2006. WCF unifies several other existing distributed communication APIs supported by the .NET Framework 2.0. Previously, separate APIs for SOAP-based communications for maximum interoperability (Web Services), binary-optimized communications between applications running on Windows machines (.NET Remoting), transactional communications (Distributed Transactions), and asynchronous communications (Message Queues) existed. WCF unified all these mechanisms into a single, common, general service-oriented programming model for communications.
The principles of Service orientation says “we don’t think in terms of objects (Object Oriented) or components (Component oriented) because these two have problems when they come in distrubuted environments. There are differences whether you talk locally (in case of objects or components developed locally) and when you are talking in a distributed environment. So we are thinking in terms of messages. We accept messages and send messages”
Four tenets of SOA and how is it implemented in WCF Technology in a way,how can WCF to avoid the well-known pitfalls of using current technologies such as (WSE):
1) Boundaries are explicit :
Applications is communicating to each other by sending and receiving messages to each other.
2) Services are autonomous: you can't control any service out of your organization boundaries.
Your solution should be loosely coupled ,so it can tolerate these changes and continue running if one or more services are un available.
3) Services share schema,contracts not classes or types: simply each service publish the schema of the data which will be exchanged between the service and clients and how can be binded to the clients,these information is used by clients to consume the published services.
4)Compatibility is based on policy:Schemas and contracts exposed by the service is define the "Shape" of the service.if you familiar with WS Enhancements,it has its specification on WS-Security,WS-Interoperability....etc which has been encapsulated into the WCF unified platform.
Additional Service Oriented principles (you should adhere to simply because it is the right thing to do) :
1. Services are secure.
2.Services leave the system in a consistent state.
3.Services are thread-safe.
4. Services are reliable & robust.
Interoperable
Scaleable
Available
Responsive
Disciplined
WCF a part of the .NET Framework that provides a unified programming model for rapidly building service-oriented applications that communicate across the web and the enterprise. It is a microsoft platform for SOA (service oriented architecture). So service oriented is a key feature of WCF. It is an attempt to do interoperability with other platforms.
It is a single extendable object model.
WCF is a core component of the .NET Framework 3.0 (formerly WinFX) which is included with Windows Vista and will support Windows 2003 and Windows XP platforms as well as the future version of Windows Server.
As its name suggests, WCF provides the .NET Framework with a basis for writing code to communicate across components, applications, and systems. 
Services expose one or more endpoints where messages can be sent by the clients in order to get some information from the service or submit some data to the service.
Each endpoint consists of 3 properties (ABC)
Address (Where) : URI indicates where the service is located.
Binding (How) : Technical implementation of the communication. It defines how i
Contract (What) : It is a technical description or interface.
Services expose one or more endpoints where messages can be sent. Each endpoint consists of an address, a binding, and a contract. The address specifies where to send messages. The binding describes how to send messages. And the contract describes what the messages contain. Clients need to know this information before they can access a service.
WCF Architecture
ABCs of WCF : Address, Binding and Contact.
When we are creating a service library, we will be applying attributes on our interfaces and classes to build something called Data Contracts and Service Contracts.
Contracts
Contracts define various aspects of the message system. It is a platform-neutral and standard way of describing what the service does.
In WCF we have 4 types of contract:
· Service Contract: Service contracts define the operations that a service will perform when executed. They tell the outside world a lot about the service such as message data types, operation locations, the protocols the client will need in order to communicate with the service, and the operations the service provides. It maps CLR types to WSDL.
Service contracts uses two types of attributes:
ServiceContract - This attribute is used to define the Interface.
OperationContract - This attribute is used to define the method inside Interface.
· Data Contract: It describes a data structure. It defines which data types can be transferred in the service. A Data Contract marks a business entity (class) as a participant in a Service Contract and Service Operation. It maps CLR types to XSD.
Data contracts uses two types of attributes:
DataContract : is used to define the class.
DataMember : is used to define the properties.
· Fault Contract: A Fault Contract is the definition of how errors are raised and handled by WCF clients. There is no concept of an exception in WCF (this is a .NET only idea). Fault Contracts describe error conditions and behavior for managing these conditions.
· Message Contract: It is an extra functionality allows you to send message in a customized way.It defines the structure of the message over the wire. It can be typed or untyped and useful when there is an existing message format to comply with. It maps CLR types to SOAP messages.
Steps to create and use a WCF service:
WCF Message Exchange Patterns
WCF service contracts can express three message exchange patterns that can be used in your
services:
1. Simplex (One way)
One-way is a “fire-and-forget” style of messaging as in this scenario, the client initiates communication and sends a message to the service without for a reply from the service. The service consumes the message and performs some action but does not communicate back to the client. The client in the Simplex message pattern suffers from short-term memory loss. When the client sends the message, it has no idea it sent a message because it is not expecting a response.
2. Duplex : It allows client and service to communicate openly by exchanging messages at both ends. It is a peer-to-peer connection.
3. Request-Reply: This is the default pattern of exchanging messages in WCF. This is the most common pattern in today’s web services (ASMX) world. In this the client sends a message(Request) and waits until a reply is sent back(Reply).
Monday, July 6, 2009
Free images
Stock.XCHNG (Tons of Free Images)
Morguefile (Also free images)
iStockPhoto (Not free, but Affordable prices)
Corbis (Excellent images but expensive)
GettyImages (One more Paid Site with good images)
Screen Capture in Windows Vista
Apple Mac 10.x have an easy to use Screen grab tool in-built in the system menu.
The good news is Windows Vista bundles (out of box) a great screen capture tool called "Snipping Tool". The tool helps you to Capture a portion of your screen so you can save, annotate, or share the image.
You can find the Snipping Tool either via Start > Accessories > Snipping Tool or by simply typing Snip into any Search window. But it is easy to create a shortcut for it by using the path %SystemRoot%\system32\SnippingTool.exe. This path should work in all Windows Vista (32 bit) editions. It also has rudimentary painting (pen) tool. The tool allows you to copy the URL associated with a screen area and you can control this in your application through this API.
Thursday, May 14, 2009
Microsoft Contracts - The newest
The concept is based on a programming model known as Design By Contract."Design by Contract" is a method made famous by Bertrand Meyer in the Eiffel programming language where support is built right into the language constructs.
Code Contracts for .NET, is a general design-by-contract mechanism that all .NET programmers can now take advantage of. Using it, programmers provide method preconditions and postconditions. Also Contracts allow you to express object invariants in your code.
The basic idea is that a class can be viewed as having a contract with its clients whereby the class guarantees to provide certain results (postconditions of its methods) provided that the clients agree to satisfy certain requirements (preconditions of the class's methods). For example, consider a routine:
FindCustomer(int customerID)
The precondition might be that customerID is positive. The postcondition might be that we guarantee to find the customer, i.e., possibly among other things, that the return value is a non-empty string. A failure of the precondition indicates a bug in the caller, the client. A failure of the postcondition indicates a bug in the routine, the supplier.
PreConditions : These are expressed in the code using Contracts.Requires(...). PostConditions : These are expressed in the code using Contracts.Ensures(...).
Object Invariants : The Contract.Invariant() method is used to specify object invariants.
All of the contract methods are static methods de ned in the Contract class which appears in the
System.Diagnostics .Contracts namespace.
The library can be downloaded from http://research.microsoft.com/en-us/downloads/4ed7dd5f-490b-489e-8ca8-109324279968/default.aspx
Wednesday, April 22, 2009
OpenID
What is OpenID?
OpenID eliminates the need for multiple usernames across different websites, simplifying your online experience.
You get to choose the OpenID Provider that best meets your needs and most importantly that you trust. At the same time, your OpenID can stay with you, no matter which Provider you move to. And best of all, the OpenID technology is not proprietary and is completely free.
For businesses, this means a lower cost of password and account management, while drawing new web traffic. OpenID lowers user frustration by letting users have control of their login.
For geeks, OpenID is an open, decentralized, free framework for user-centric digital identity. OpenID takes advantage of already existing internet technology (URI, HTTP, SSL, Diffie-Hellman) and realizes that people are already creating identities for themselves whether it be at their blog, photostream, profile page, etc. With OpenID you can easily transform one of these existing URIs into an account which can be used at sites which support OpenID logins.
OpenID is still in the adoption phase and is becoming more and more popular, as large organizations like AOL, Microsoft, Sun, Novell, etc. begin to accept and provide OpenIDs. Today it is estimated that there are over 160-million OpenID enabled URIs with nearly ten-thousand sites supporting OpenID logins.
OpenID is an open protocol that enables a person to use a URL as an identity and use the same identity (the URL) at multiple web sites that support OpenID. Web- enabled applications can use the identity URL for authentication, authorization, and other purposes. It is a relatively new concept which puts the control of the identity into the hands of its owner, the end user. The owner of the identity can decide, and has control over, which information should be presented to an application or web site for authentication purpose.
Among other things, OpenID enables owners to:
· Login to web-enabled applications and web sites without ever entering any username and password information.
· Enable web sites to request information from a user; and empowering the user to choose which information is to be sent to a web site during authentication/authorization process.
· Chose which sets of information (also known as profiles or cards) to be sent to different web sites, based upon need and risk level.
· Allows implementation of graded and risk-based authorization.
· Implement an alternate to single sign on (SSO) for multiple applications within an organization.
· Implement an alternate mechanism for cross-company authentication (CCA) for affiliates and business partners.
· Integrate applications into the OpenID system using a simple and elegant mechanism.
· Lower cost of implementation and maintenance of an identity management solution.
Who Owns or Controls OpenID?
OpenID has arisen from the open source community to solve the problems that could not be easily solved by other existing technologies. OpenID is a lightweight method of identifying individuals that uses the same technology framework that is used to identify websites. As such, OpenID is not owned by anyone, nor should it be. Today, anyone can choose to be an OpenID user or an OpenID Provider for free without having to register or be approved by any organization.
The OpenID Foundation was formed to assist the open source model by providing a legal entity to be the steward for the community by providing needed infrastructure and generally helping to promote and support expanded adoption of OpenID.
As Brad Fitzpatrick (the father of OpenID) said, “Nobody should own this. Nobody’s planning on making any money from this. The goal is to release every part of this under the most liberal licenses possible, so there’s no money or licensing or registering required to play. It benefits the community as a whole if something like this exists, and we’re all a part of the community.”
Terminology
1. Identifier : URI or XRI
2. Replying party (RP, Consumer)
3. openID provider (Identity provider, openID server)
There are three major components in any OpenID system: Consumer, Identity Provider, and User Agent. These components interact with each other during the authentication process. Roles for these components are explained next.
1. The Consumer, which is the web site where you are trying to login, interacts with the Identity Provider and the User Agent (the web browser). An End User will try to login to the Consumer web sites using OpenID. During the authentication process, the Consumer will send some messages to the Identity Provider directly as well as via User Agent with the help of HTTP redirect messages.
2. The Identity Provider is the OpenID server that holds an End User’s
credentials. The Identity Provider will validate the ownership of an identity URL to the Consumer using two basic mechanisms which we shall discuss later in this chapter.
3. An End User will interact with the Consumer and Identity Provider using the User Agent. The User Agent is your web browser.
During the authentication process, the browser acts as the middle man between the Identity Provider and the Consumer web site for some messages. Typically, a Consumer will interact with the web browser as well as the Identity Provider during authentication process. However in some cases, the Consumer may use cached keys to authenticate a user without any direct communication with the Identity Provider.
There are two basic communications methods among different entities in an OpenID system:
1. Direct Communication
2. Indirect Communication.
In the Direct Communication mechanism, two entities directly talk to each other using the HTTP protocol. The HTTP POST method is used for direct communication.
With the Indirect Communications, two entities talk to each other via a third entity. This third entity is typically the web browser. Indirect communication may happen via HTTP Redirect or via HTML Form redirection.
OpenID has two major modes of operation: the Dumb mode and the Smart mode. These modes are based upon how intelligent the Consumer is. In Dumb mode, as the name implies, the consumer is not that smart and has to perform few additional steps every time a user logs in. In Smart mode, the Consumer keeps state information and caches shared keys for future use.
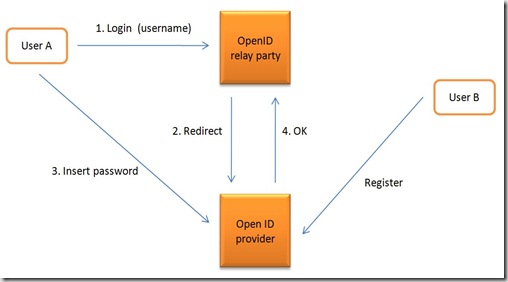
Dumb Mode Communications Flow
1. You visit the Consumer web site where you want to login.
2. The web site presents a web page where you enter your identity URL. Typically, you will enter your Identity URL (for ex http://myvikas.myopenid.com) and click on Login button. Different web sites may have different types of web pages but the process will remain the same.
3. The Consumer web site will clean up the Identifier URL and fetch the information from its current URL location. . In OpenID specification version 2, another XML protocol, known as Yadis, can also be used at this stage for service discovery.
4. After fetching the page, the Consumer will then parse it and determine the location of Identity Provider (OpenID Server). This parsing process is also called discovery. After parsing, the Consumer will then redirect the web browser to the Identity Provider to obtain the assertion information. This happens using the HTTP GET method. Optionally, the consumer may establish a connection with the identity provider at this point and exchange a shared secret for further communication. This is shown with a dotted line in Figure and marked as step 4a.
5. If the end user is not already logged into to Identity Provider, the Identity Provider may ask the End User to login. However, it should be noted that this part is outside the OpenID specifications and it is left to the Identity Provider to decide how to authenticate the End User. In some circumstances, if you have already logged into the Identity Provider web site, this part may be skipped altogether.
6. The Identity Provider website will return the assertion information with its signature to the Consumer via browser redirect. This assertion will represent either an authentication success or failure. The HTTP GET method is used in this step as well. Note that this is the Indirect Communication between Identity Provider and the Consumer.
7. During successful assertion, the Consumer will establish a direct connection with the Identity Provider, preferably over a secure SSL session. It will request the authentication information directly from the Identity Provider and compare it with the assertion information it received via User Agent (web browser). This is to double check the validity of the assertion in case a User Agent (or a malicious attacker) is trying to cheat.
8. If there is a match in the previous step, the End User will login to the website. Otherwise the login will fail.
Smart mode communication is almost same except a change in point-7. It is :
After a successful assertion, the Consumer verifies the assertion using the cached shared key. If there is a match in the previous step, the End User will login to the web site. Otherwise login will fail.
Detailed diagram of openID protocol:
There are a lots of terms like XRDS, yadis described in this diagram. I will expore these terms soon in deeper detail.
Monday, April 20, 2009
Mashup
A mashup is a website or web application that seamlessly combines content from more than one source into an integrated experience.Content used in mashups is typically sourced from a third party via a public interface or API. Other methods of sourcing content for mashups include Web feeds (e.g. RSS or Atom) and JavaScript.Many people are experimenting with mashups using eBay, Amazon, Google, and Yahoos APIs. The increased use and popularity of mashups has increased with the emergence of Web 2.0, which is characterized by active user participation and interaction.The architecture of mashup web applications is always composed of three parts:• The content provider: it is the source of the data. Data is made available using an API and different Web-protocols such as RSS, REST, and Web Service• The mashup site: is the web application that provides the new service using different data sources that are not owned by it.• The client web browser: is the user interface of the mashup. In a web-application, the content can be mashed by the client web browsers using client side web language for example JavaScript.Types of Mashups:There are many types of mashups, such as consumer mashups, data mashups, and business mashups. Consumer mashups: Consumer mashups combine different forms of media from multiple sources and combine them into a single graphical interface. Consumer mashups are aimed at the general public, that is, consumers. Examples of consumer mashups include the many Google Maps applications, iGuide and Radioclouds.Data mashups:Data mashups combine similar types of media and information from multiple sources into a single graphical representation. An example of a data mashup is the Havaria Information Services' AlertMap. which combines current data from over 200 sources related to severe weather conditions, biohazard threats and seismic information from around the world, and displays them on a single map of the world. Another example of a data mashup is Yahoo PipesBusiness mashups:Business mashups focus on various forms of data aggregation into a single presentation, but also allow for collaborative function ability amongst businesses and developers. Serena Software is a company involved in the business mashup industry.
Thursday, April 9, 2009
OAUTH
What does OAuth really mean?
Well, lets break the above description down into some key phrases and the pieces should come together.
A "Protocol" is a standardized method for the communication of two computers. For instance HTTP is the standardized way of a webserver communicating with your computer when you browse a website.
"Open” comes from the fact that this protocol is open source and can be viewed, downloaded, and maintained by anyone who is willing to take up the torch.
“Secure API authorization” is the functionality that OAuth.net gives to its stakeholders - the ability for a developer to download OAuth.net and secure their API access without having to write a unique (and possibly bug filled) authentication!
The key tenet of these schemes and of OAuth is that users should be able to share their data with third-party applications without sharing their passwords.
OAuth allows you to share your private resources (photos, videos, contact list, bank accounts) stored on one site with another site without having to hand out your username and password. There are many reasons why one should not share their private credentials. Giving your email account password to a social network site so they can look up your friends is the same thing as going to dinner and giving your ATM card and PIN code to the waiter when it’s time to pay. Any restaurant asking for your PIN code will go out of business, but when it comes to the web, users put themselves at risk sharing the same private information. OAuth to the rescue.
Both the valet key and ATM cards are good metaphors for OAuth from a user perspective. Instead of giving your ATM card and PIN code, the card can double as a credit card with a signature authorization. Just like your username and password provide full access to your resources, your ATM card and PIN code provide you with great control over your bank accounts – much more than just charging goods. But when you replace the PIN code with your signature, the card becomes very limited and can only be used for limited access.
Users don’t care about protocols and standards – they care about better experience with enhanced privacy and security. This is exactly what OAuth sets to achieve. With web services on the rise, people expect their services to work together in order to accomplish something new. Instead of using a single site for all their online needs, users use one site for their photos, another for videos, another for email, and so on. No one site can do everything better. In order to enable this kind of integration, sites need to access the user resources from other sites, and those are many times protects (private family photos, work documents, bank records). They need a key to get in.
The key used by users is usually a combination of username and password. This can be an OpenID or any other login credential. But this key is too powerful and unrestrictive to share around. It also cannot be unshared once handed out except for changing it which will void access to every site, not just the one the user intends to block. OAuth addresses that by allowing users to hand out tokens instead. Each token grants access to a specific site (a video editing site) for specific resources (just videos from last weekend) and for a defined duration (the next 2 hours).
Unlike OpenID where users must do something first - get an OpenID identity they can use to sign-into sites – OAuth is completely transparent to the users. In many cases (if done right), the end-user will not know anything about OAuth, what it is or how it works. The user experience will be specific to the implementation of both the site requesting access and the one storing the resources, and adjusted to the device being used (web browser, mobile phone, PDA, set-top box).
A typical example is when a user wants to print a photo stored on another site. The interaction goes something like this: the user signs into the printer website and place an order for prints. The printer website asks which photos to print and the user chooses the name of the site where her photos are stored (from the list of sites supported by the printer). The printer website sends the user to the photo site to grant access. At the photo site the user signs into her account and is asked if she really wants to share her photos with the printer. If she agrees, she is sent back to the printer site which can now access the photos. At no point did the user share her username and password with the printer site.
Some Definitions
Service Provider: A web application that allows access via OAuth.
User: An individual who has an account with the Service Provider.
Consumer: A website or application that uses OAuth to access the Service Provider on behalf of the User.
Protected Resource(s): Data controlled by the Service Provider, which the Consumer can access through authentication.
Consumer Developer: An individual or organization that implements a Consumer.
Consumer Key: A value used by the Consumer to identify itself to the Service Provider.
Consumer Secret: A secret used by the Consumer to establish ownership of the Consumer Key. Request Token: A value used by the Consumer to obtain authorization from the User, and exchanged for an Access Token.
Access Token: A value used by the Consumer to gain access to the Protected Resources on behalf of the User, instead of using the User’s Service Provider credentials.
Token Secret: A secret used by the Consumer to establish ownership of a given Token.
OAuth Protocol Parameters: Parameters with names beginning with oauth_.
There are some libraries develolped for implementing OAUTH. I recommennd DNOA (DontNetOpenAuth) written by Andrw Arnott. You can even get the Full source code of this including Mock tests as it is Open Source.
I have implemented OAuth and OpenID in one of my project using this DotNetOpenAuth library. To get it please write to me at cybertechie.india@gmail.com
Monday, March 23, 2009
Install Windows Vista from a USB 2.0 Flash Drive
The USB flash drive will have an address like this "disk 1", but we will continue to refer to it as "disc x" where "x" is the number of the drive on your computer. You will now need to enter the following commands:
1. diskpart
2. select disk 1
3. clean
4. create partition primary
5. select partition 1
6. active
7. format fs=fat32
8. assign
9. exit
Using "xcopy d:*.* /s/e/f e:", simply copy the entire content of the Windows Vista DVD on the flash drive. Boot the computer from the USB drive and simply install Windows Vista.
Wednesday, March 11, 2009
Motivations
Experience is that marvelous thing that enables you to recognize a mistake when you make it again.
—F. P. Jones
Logic is the art of going wrong with confidence.
—Joseph Wood Krutch
Health is merely the slowest possible rate at which one can die.
—anonymous
I find that the harder I work, the more luck I seem to have.
—Thomas Jefferson
Q: What are the most exciting, promising software engineering ideas or techniques on the horizon?
A: I don't think that the most promising ideas are on the horizon. They are already here and have been for years, but are not being used properly.
—David L. Parnas
Ours is too great and too complex a nation for even such as I to direct and lead every action.
—Attila the Hun
It's easy to have a complicated idea.
It's very very hard to have a simple idea.
—Carver Mead
The true measure of a man is how he treats someone who can do him absolutely no good.
—Samuel Johnson
There is only one move that really counts: the next one.
—Chess master Jose Capablanca
I have often regretted my answers, never my silence.
—adapted from Xenocrates
"You are your greatest investment. The more you store in that mind of yours, the more you enrich your experience, the more people you meet, the more books you read, and the more places you visit, the greater is that investment in all that you are. Everything that you add to your peace of mind, and to your outlook upon life, is added capital that no one but yourself can dissipate." -George Matthew Adams
"So long as millions live in hunger and ignorance, I hold every man as traitor" Vivekananda
Visualize your Goals - an article.
The Catalina Island is twenty-one miles away from the coast of California, and many people have taken the challenge to swim across it. On July 4th 1952, Florence Chadwick stepped into the water off Catalina Island to swim across to the California coast. She started well and on course, but later fatigue set in, and the weather became cold. She persisted, but fifteen hours later, numb and cold, she asked to be taken out of the water.
After she recovered, she was told that she had been pulled out only half a mile away from the coast. She commented that she could have made it, if the fog had not affected her vision and she would have just seen the land. She promised that this would be the only time that she would ever quit.She went back to her rigorous training. And two months later she swam that same channel. The same thing happened. The fatigue set in, and the fog obscured her view, but this time she swam with faith and vision of the land in her mind. She knew that somewhere behind the fog was land. She succeeded and became the first woman to swim the Catalina Channel. She even broke the men’s record by two hours.
SUCCESS PRINCIPLES:
When you set your goal, keep pressing on even when you are tired, physically and mentally, and even though there are many challenges ahead.
Keep the vision of your goal crystal clear before you and never, never, never… give up!
See the reaching, commit to it, and you will surely see your goal realized.
"One of the illusions of life is that the present hour is not the critical, decisive hour. Write it on your heart that every day is the best day of the year."*********Today is an important day. That problem you solve, that decision you make, that time you enjoy can shape your whole life. The way you and I approach today, and each day, is crucial. Our lives are built by a series of days like today." -- Ralph Waldo Emerson
An affirmation that can help in living each day fully :
Today I will live through the next 24 hours and not try to tackle all of life's problems at once.
Today I will improve myself, body, mind and spirit.
Today I will refuse to spend time worrying about what might happen if...
Today I will not imagine what I would do if things were different. They are not different. I will do my best with what material I have.
Today I will find the grace to let go of resentments of others and self-condemnation over past mistakes.
Today I will not try to change, or improve, anybody but me.
Today I will act toward others as though this will be my last day on earth.
Today I will be unafraid. I will enjoy what is beautiful, and I will believe that as I give to the world, the world will give to me.
Whether these are the best of times or the worst of times, these are the only times we've got. Live each day fully and you will look back on a life that made a DIFFERENCE.
* Winning isn't everything. But wanting to win is.
* You would achieve more, if you don't mind who gets the credit.
* When everything else is lost, the future stillremains.
* Don't fight too much. Or the enemy would know your art of war.
* The only job you start at the top is when you dig a grave.
* If you don't stand for something, you'll fall for everything.
* If you do little things well, you'll do big ones better.
* Only thing that comes to you without effort is old age.
* You won't get a second chance to make the first impression.
* Only those who do nothing do not make mistakes.
* Never take a problem to your boss unless you have a solution.
* If you are not failing you're not taking enough risks.
* Don't try to get rid of bad temper by losing it.
* If at first you don't succeed, skydiving is not for you.
* Those who don't make mistakes usually don't make anything
* There are two kinds of failures. Those who think and never do, and those who do and never think.
* Pick battles big enough to matter, small enough to win.
* All progress has resulted from unpopular decisions.
* Change your thoughts and you change your world.
* Understanding proves intelligence, not the speed of the learning.
* There are two kinds of fools in this world. Those who give advise and those who don't take it.
* The best way to kill an idea is to take it to a meeting.
* Management is doing things right. Leadership is doing the right things.
* Friendship founded on business is always better than business founded on friendship.
SECRET OF SUCCESS
A young man asked Socrates the secret of Success. Socrates told the young man to meet him near the river the next morning. They met.Socrates asked the young man to walk with him towards the river.When the water got up to their neck, Socrates took the young man by surprise and ducked him into the water. The man struggled to get out but Socrates was strong and kept him there until he started turning blue.The young man struggled hard and finally managed to get out and the first thing he did was to gasp and take deep breath. Socrates asked 'What you wanted the most when you were there?' The man replied 'Air'.Socrates said 'that's the most secret to success. When you want success as badly as you wanted air, you will get it. There is no other secret'.
Monday, February 23, 2009
Unit Testing
As soon as the programmer develops a unit of code, unit is tested for varous scenarios. As the application is built it is much more economical to find and eliminate the bugs early on. Hence unit testing is the most important of all the testing levels. As the software project progresses ahead, it becomes more and more costlier to find and fix the bugs. In most cases it is developer's responsibility to deliver the Unit-Tested code.
Unit Test Tasks and Steps :
1. Create a Test Plan.
2. Create Test cases and Test Data.
3. If applicable create scripts to run the test cases.
4. Once the code is ready execute the test cases.
5. Fix the bugs if any and retest the code.
6. Repeat the cycle until the unit is free of all the bugs.
Unit tests inspect both black boxes or white boxes.
Black Box Test
A black box test (also known as a "functional test") is one in which you feed it inputs and verify the outputs without being able to inspect the internal workings. Furthermore, one doesn't usually have information regarding:
1. how the box handles errors.
2. whether your inputs are executing all code pathways.
3. how to modify your inputs so that all code pathways are executed.
4 The dependencies on other resources.
Black box testing limits your ability to thoroughly test the code, primarily because the you don't know if you're testing all the code pathways. Typically, a black box test only verifies that good inputs result in good outputs (hence the term "functional test").
Classes are often implemented as black boxes, giving the "user" of the class access only to the public methods and properties that the implementer selected.
White box Test:
A white box provides the information necessary to test all the possible pathways. This includes not only correct inputs, but incorrect inputs, so that error handlers can be verified as well. This provides several advantages:
1. You know how the box handles errors
2. You can usually write tests that verify all code pathways
3. The unit test, being more complete, is a kind of documentation guideline that the implementer can use when actually writing the code in the box
4. Resource dependencies are known.
5. Internal workings can be inspected.
In the "write the test first" scenario, the ability to write complete tests is vital information to the person that ultimately implements the code, therefore a good white box unit test must ensure that, at least conceptually, all the different pathways are exercised.
Another benefit of white box testing is the ability for the unit test to inspect the internal state of the box after the test has been run. This can be useful to ensure that internal information is in the correct state, regardless of whether the output was correct. Even though classes are often implemented with many private methods and accessors. with C# and reflection, unit tests can be written which provide you the ability to invoke private methods and set/inspect private properties.
Code Coverage
Although there may be occasional exceptions, we need our tests to cover most of our code. 100% code coverage might be too high a goal to reach for right now, but we need to have a high percentage of the code we right covered in our testing.
There are a number of coverage criteria, the main ones being:
Function coverage - Has each function in the program been executed?
Statement coverage - Has each line of the source code been executed?
Decision coverage (also known as Branch coverage) - Has each control structure (such as an if statement) evaluated both to true and false?
Condition coverage - Has each boolean sub-expression evaluated both to true and false (this does not necessarily imply decision coverage)?
Modified Condition/Decision Coverage (MC/DC) - Has every condition in a decision taken on all possible outcomes at least once? Has each condition been shown to affect that decision outcome independently?
Path coverage - Has every possible route through a given part of the code been executed?
Entry/exit coverage - Has every possible call and return of the function been executed?
NCover is a useful tool for exploring how much of your code is covered by a single test or a suite of tests. It is an open source application, like NUnit.
The Visual Studio Team Test Edition also has a built-in code.
Unit Testing Patterns
Pass/Fail Patterns
The Simple-Test Pattern
The Code-Path Pattern
The Parameter-Range Pattern
Data Driven Test Patterns
The Simple-Test-Data Pattern
The Data-Transformation-Test Pattern
Data Transaction Patterns
The Simple-Data-I/O Pattern
The Constraint-Data Pattern
The Rollback Pattern
Collection Management Patterns
The Collection-Order Pattern
The Enumeration Pattern
The Collection-Constraint Pattern
The Collection-Indexing Pattern
The Performance-Test Pattern
Process Patterns
The Process-Sequence Pattern
The Process-State Pattern
The Process-Rule Pattern
Simulation Patterns
Mock-Object Pattern
The Service-Simulation Pattern
The Bit-Error-Simulation Pattern
The Component-Simulation Pattern
Multithreading Patterns
The Signalled Pattern
The Deadlock-Resolution Pattern
Stress-Test Patterns
The Bulk-Data-Stress-Test Pattern
The Resource-Stress-Test Pattern
The Loading-Test Pattern
Presentation Layer Patterns
The View-State Test Pattern
The Model-State Test Pattern
Code Smells
A code smell is a surface indication that usually corresponds to a deeper problem in the system.
Test Driven Development
being tested. This allows you to focus on your interface and what you expect from your code
prior to focusing on its particular implementation.
The testing components for implementing a test-driven development plan are known as unit
tests.
Test-driven software development technique requires that an automated unit test, defining requirements of the code, is written before each aspect of the code itself. These tests contain assertions that are either true or false.
In test-driven development, each feature begins with writing a test, so for each method, the developer should have to write a unit tests related case. Every method will have more than one test case depending on the complexity of the method signature.
Test-driven development gives developers the confidence to make changes to the system,
because they know that the tests will tell them if they have broken anything and where in the
application the break occurred. This is one of the most effective feedback mechanisms that
the development team can have for ensuring stability and high quality.
Another advantage to test-driven development is that it assists in keeping the code simple.
When developers take a code-first approach to development, they have a tendency to
design as they code, without having a clear picture as to what they want to achieve. They
basically let the creative process lead them to a design while they are coding. This often does
not result in the most straightforward solutions. In fact, in many cases, it results in an overly
complicated design. Test-driven development forces developers to think about the outcome of
what they are developing, and then simply code until the test passes, which leads to a simpler
design. This is called development by intention.
Best practices of using TDD:
1. Write the test first, then the code.
Reason: This ensures that you write testable code and that every line of code gets tests written for it.
2. Design classes using dependency injection.
Reason: You cannot mock or test what cannot be seen.
3. Separate UI code from its behavior using Model-View-Controller or Model-View-Presenter.
4. Do not write static methods or classes.
5. Program off interfaces, not classes.
Reason: Interfaces can be easily mocked using Rhino Mocks and other mocking frameworks.
6. Isolate external dependencies.
Test-Driven Development is a software development technique consisting of short iterations where new test cases covering the desired improvement or new functionality are written first, then the production code necessary to pass the tests is implemented, and finally the software is refactored to accommodate the changes.
Requires test automation
"Keep It Simple, Stupid" (KISS [^]) principle
"You Ain't Gonna Need It" (YAGNI [^]) principle
"Fake it, till you make it" principle
Requires techniques, such as discussion and code reviews for example, to ensure not only that the correct features are implemented, but that the resulting code uses acceptable styles.